Firefox XPS IRC Attack
Content
Since it's been copied to much less sweet websites (without credit or sourcing), it's time to write up a security advisory (I believe the publishing of infosec advisories is a first for Encyclopedia Dramatica, [[lulz]]) and let everybody know whats up. [[Firefox]] has a hole in its port blocking scheme that allows a clever [[troll]] to spam an unsuspecting IRC daemon with whatever he desires. The [[GNAA]] leveraged this vulnerability to bring complete ruin upon the [[Freenode]] [[IRC]] network.
==How it works==
A new implementation of http://www.kb.cert.org/vuls/id/476267" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">cross-protocol scripting was used to automatically fill a HTTP form to send a POST to port 6667 and shove a bunch of IRC commands down the socket. Although Mozilla http://www.mozilla.org/projects/netlib/PortBanning.html" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">banned most of the fun ports years ago, 6667 -- the default port for IRC servers, wasn't on the list. In all likelihood, this the first use of this attack in the wild, ever.
This attack has a lot of implications outside of IRC. Think of all the other TCP ports that are in common use these days that aren't covered in Mozilla's banned list. Most protocols do not use a cookied handshake of any sort to initiate a connection. The sheer amount of potential that exists in turning a web browser into a device speaking an arbitrary protocol is huge. For example, SIP protocol can run on TCP these days. You can make someone's web browser interact with a SIP device. All sorts of potentially criminal and civil liability generating applications. Expect more of them to appear out of the GNAA labs in the future!
{{cs|SectionOne|Example source (click plus to uncollapse)|
|0}}
Browser rundown
*[[Firefox]] affected, all versions
*Seamonkey affected, all versions
*Mozilla suite affected, all versions
*Possibly others affected
*[[Microsoft]] [[Internet Explorer]], [[Apple]] Safari unaffected. [[Lie|Because closed-source commercial products are simply better.]]
IRCD rundown
*Efnet, no longer affected (took them about an hour to enact countermeasures)
*[[Buttes]]net, no longer affected. (took them about 4 hours to enact countermeaures)
*OFTC, no longer affected (took them about a day)
*Freenode, over 1 month to enact countermeasures with a server upgrade from Hyperion to ircd-seven, after which they immediately got raped by GNAA. (LOL)
Best things that were done to Freenode
*Embedded exploit in hidden iframes in [[Last Measure|everyone's favorite shock site]], leading to thousands of hosts joining network.
*Messaged Freenode opers blog links with hidden iframes and watched as they all k-lined eachother
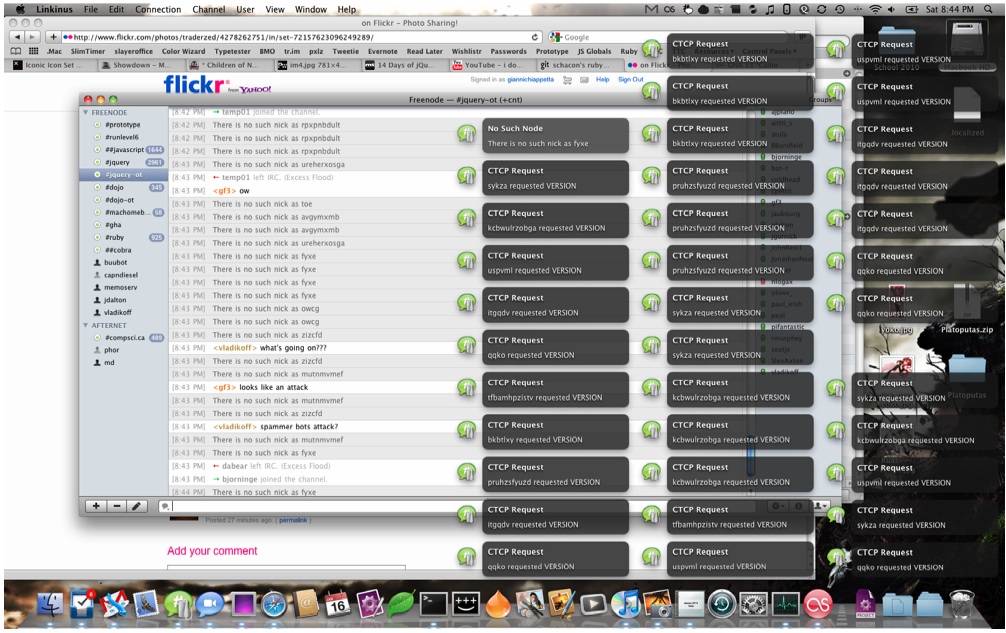 http://typicalmacintoshuser.com" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">Typical Macintosh User" class="max-w-full h-auto rounded-lg shadow-md border border-gray-300 dark:border-gray-600" style="max-width: 250px;" loading="lazy" onerror="this.onerror=null; this.src='/images/missing.png'; this.alt='Image not found: Lolgrowl.jpg';">
http://typicalmacintoshuser.com" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">Typical Macintosh User" class="max-w-full h-auto rounded-lg shadow-md border border-gray-300 dark:border-gray-600" style="max-width: 250px;" loading="lazy" onerror="this.onerror=null; this.src='/images/missing.png'; this.alt='Image not found: Lolgrowl.jpg';">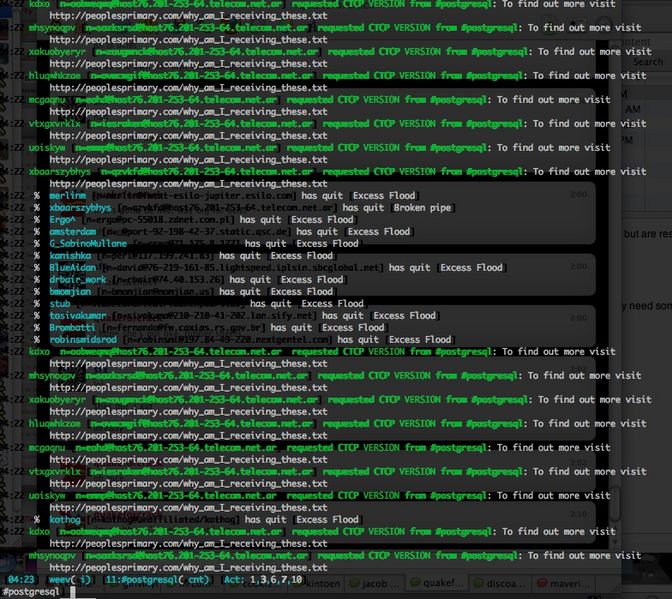
*Switched up the floods to CTCP and made users flood themselves off with CTCP replies over and over again until they were k-lined from servers with reconnect limits.
*Flooded freenode with channel names full of legitimate users implying they were troll channels, making paranoid freenode ops ban their own legitimate users.
*After seeing a Freenode staff member make a bot that automatically k-lined flooding users in a channel with wildcards, manually flooded the channel from a shell account and watched it ban an entire TLD, taking a gigantic swath of the network with it.
*Made Freenode staff xenophobic and paranoid and watched them k-line anyone who dared ask for assistance or complain about the floods.
*Making Freenode users self-propagate the link on third party blogging services with warnings to not click the link (we got huge referrals from Twitter, thanks dudes)
You are mean. Why did you torture freenode so much?
Freenode/PDPC is a fucking fraud. In the entire time it has existed, it has never released financial statements. [[Rob Levin]] used PDPC to embezzle hundreds of thousands of dollars which should have been given to open source development projects. He faked his death, and came back in this "christel" incarnation in Europe to continue embezzling from Freenode. It is all a big lie, and these people should be thrown into ovens. EFnet continuously hosts 100x the number of users that Freenode does without constant netsplits and incidents. OFTC does not sit there and continuously beg for money. Get off of Freenode. Go to somewhere that is ethical.
Beyond that, the trolling scene has a lot invested in ruining Freenode. I http://antisec.wordpress.com/2006/06/27/eyeballing-rob-levin/" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">posted Rob Levin's social security number, enabling the series of identity thefts and ruins that forced the man to fake his death. With [[Bantown]], I watched Jmax http://it.slashdot.org/article.pl?sid=06/06/25/1440236" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">sniff lilo's oper block password off the wire and absolutely wreck the network in it. I also watched [[Grog]] (of the [[GNAA]] at the time, until he was excommunicated by the former tyrant [[timecop]]) convince lilo that he was the founder of MySQL, get opered up, wreck the network. Then he convinced lilo that his daughter's computer was hacked, apologized, got his o:line back and wrecked the network again.
In short, wrecking Freenode is a long and glorious troll tradition that stretches backwards for time immemorial. If you associate with Freenode, use Freenode, or support Freenode, you are a target. You are asking to be destroyed.
See Also
*[[Safari XPS Attack]]
External Links
*http://blog.freenode.net/2010/01/javascript-spam/" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">Freenode publically admitting they cant figure out iptables, pf, or snort and a simple shell script
*http://www.theregister.co.uk/2010/01/30/firefox_interprotocol_attack/" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">The Register: Firefox-based attack wreaks havoc on IRC users
*http://news.softpedia.com/news/Firefox-Bug-Used-to-Harass-an-Entire-IRC-Network-133613.shtml" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">Softpedia: Firefox Bug Used to Harass Entire IRC Network
*http://www.irc-junkie.org/2010-03-01/unrealircd-team-releases-patch-against-firefox-xps-attack/" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">IRC-Junkie: UnrealIRCd team releases patch against Firefox XPS Attack
Non-English sources
*http://teknoloji.milliyet.com.tr/firefox-ile-hack-lediler-/internet/haberdetay/01.02.2010/1193390/default.htm" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">Milliyet, Firefox ile hack'lediler!, Turkish
*http://www.xakep.ru/post/50949/default.asp" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">Xakep, Эксплоит для бреши в Firefox позволил хакерам внести хаос в работу IRC-сетей, Russian
*http://www.gulli.com/news/firefox-schwachstelle-erm-glicht-angriff-auf-irc-netze-2010-02-01" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">Gulli, Firefox-Schwachstelle ermöglicht Angriff auf IRC-Netze, German
*http://techworld.nl/technologie/16665/bug-in-firefox-gebruikt-tegen-irc-netwerk.html" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">Techworld.nl (IDG), Bug in Firefox gebruikt tegen IRC netwerk, Dutch
*http://hup.hu/cikkek/20100130/firefox_xps_bug_a_firefox_sebezhetoseget_kihasznalva_floodoltattak_az_irc_csatornakat" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">Hungarian Unix Portal, Firefox XPS bug - a Firefox sebezhetőségét kihasználva floodoltatták az IRC csatornákat, Hungarian
*http://www.azpoint.net/software/sicurezza/18247/Mozilla-bug-manda-in-crisi-Freenode-IRC.asp" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">AZPoint, Mozilla: bug manda in crisi Freenode IRC, Italian
*http://www.logiciel.net/une-faille-firefox-utilisee-pour-attaquer-freenode-un-reseau-irc-4864.htm" class="text-indigo-600 dark:text-indigo-400 hover:underline" target="_blank" rel="noopener noreferrer">Logiciel, Une faille Firefox utilisée pour attaquer Freenode, un réseau IRC, French
This template inserts specific content or formatting. View template page for more details.
This template inserts specific content or formatting. View template page for more details.
This template inserts specific content or formatting. View template page for more details.
This template inserts specific content or formatting. View template page for more details.
This template inserts specific content or formatting. View template page for more details.
| [[Encyclopedia Dramatica:Article of the Now|Preceded]] by | [[Encyclopedia Dramatica:Article of the Now|Succeeded]] by |
This template inserts specific content or formatting. View template page for more details.
[[Category:Trolls]]
[[Category:Softwarez]]
[[Category:Internets Phenomena]]
[[Category:Drama-generating techniques]]
[[Category:2010]]
Page Information
Page Details
- Page ID:
- 7789
- Namespace:
- 0
- Redirect:
- No
Latest Revision
- Revision ID:
- 47891
- Updated:
- 6 years ago
- Size:
- 11691 bytes